For a long time, Apple users believed that Mac devices were virtually immune to viruses and malware. This perception was largely due to the relatively small market share that Macs held in comparison to Windows PCs, making them less appealing to cybercriminals. However, as the popularity of Mac devices has grown, so has the interest of hackers in targeting them. Here’s why:
1. Increasing Market Share
- Growing Popularity: The increasing adoption of Mac devices, especially in professional and creative fields, has made them more attractive to cybercriminals. The more people use Macs, the more incentive hackers have to develop malware that can exploit these systems.
- High-Value Targets: Macs are often used by individuals and businesses that handle sensitive data, making them valuable targets for hackers looking to steal information or hold data ransom.
2. Misconception of Immunity
- False Sense of Security: Many Mac users still believe that their devices are inherently secure and don’t require additional protection. This misconception leads to lax security practices, such as not using antivirus software, which makes Macs more vulnerable to attacks.
- Targeting the Unprepared: Hackers exploit this false sense of security, knowing that many Mac users are less likely to take precautions against malware, making them easier targets.
3. Advanced Persistent Threats (APTs)
- Sophisticated Attacks: Hackers are increasingly using advanced persistent threats (APTs) to target specific individuals or organizations. These attacks are designed to go undetected for long periods, allowing hackers to gather information, steal data, or plant backdoors in the system.
- Targeting High-Profile Users: Mac users often include high-profile individuals in the tech, entertainment, and business sectors, who may be targeted for their valuable data or intellectual property.
4. Emergence of Mac-Specific Malware
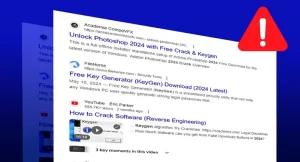
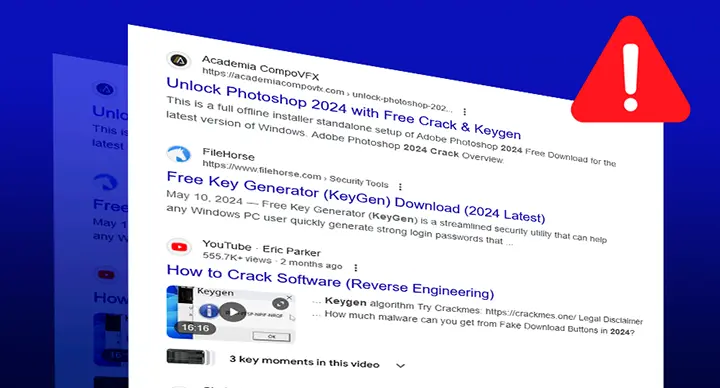
- Mac-Targeted Malware: In recent years, there has been a notable increase in malware specifically designed to target Mac devices. This includes everything from ransomware and spyware to adware and phishing attacks tailored for Mac users.
- Custom Exploits: Cybercriminals are creating custom exploits that take advantage of vulnerabilities unique to macOS, making it harder for traditional antivirus solutions to detect and neutralize these threats.
5. Exploiting Third-Party Software
- Vulnerable Applications: Many attacks on Macs exploit vulnerabilities in third-party software rather than the macOS itself. Applications like Adobe Flash, Microsoft Office, and even browsers like Safari and Chrome can serve as entry points for malware.
- Software Supply Chain Attacks: Hackers may also target the software supply chain, compromising trusted third-party applications that are widely used on Mac devices, leading to widespread infections.
6. Cross-Platform Threats
- Shared Codebases: With the rise of cross-platform applications, malware that can target both Windows and Mac systems has become more common. Hackers develop malware that can infect both operating systems, increasing the potential impact of their attacks.
- Shared Networks: Macs on networks that include Windows machines can become vectors for malware, especially in mixed-OS environments like businesses or schools.
7. The Rise of Mobile Threats
- Targeting iOS and macOS: As macOS and iOS are closely related, attackers who develop malware for one platform may find it easier to adapt their attacks to the other. The growing integration between Apple’s devices means that a breach in one could potentially compromise another.
- Phishing Attacks: Cybercriminals often use phishing attacks to gain access to Apple ID credentials, which can then be used to compromise both iOS and macOS devices.
Conclusion
As Macs become more popular, the perception of them being immune to malware is increasingly outdated. Hackers are continually developing new ways to exploit vulnerabilities in macOS and related software. This makes it more important than ever for Mac users to adopt robust cybersecurity practices, including the use of reliable antivirus software, regular system updates, and cautious online behavior. By staying informed and proactive, Mac users can better protect their devices from the growing array of cyber threats.